Earlier this year, Alpha, ZeroFOX’s cybersecurity research team has bought latest phishing kit from 16Shop for decoding it’s exploiting methodology. They found that the developed kit of 16Shop consisted of PayPal and American Express templates as new additional services. The code if this phishing kit has 16Shop signatures all over.
The New Kit
16Shop is from a typical industry as Malware-as-a-service (MaaS), which is developed by a team called the Indonesian Cyber Army. And the new updated version of this phishing kit contained PayPal and American Express templates with advanced anti-detecting features. It has three anti-bot and anti-indexing features, both defending against antivirus softwares. The kit has a blacklist.dat for blacklisting the file, an open-source anti-crawling library called CrawlerDetect and an antibot seamless integration. All these blocks antivirus software crawlers and scans to avoid flagging.
Sophisticated Service
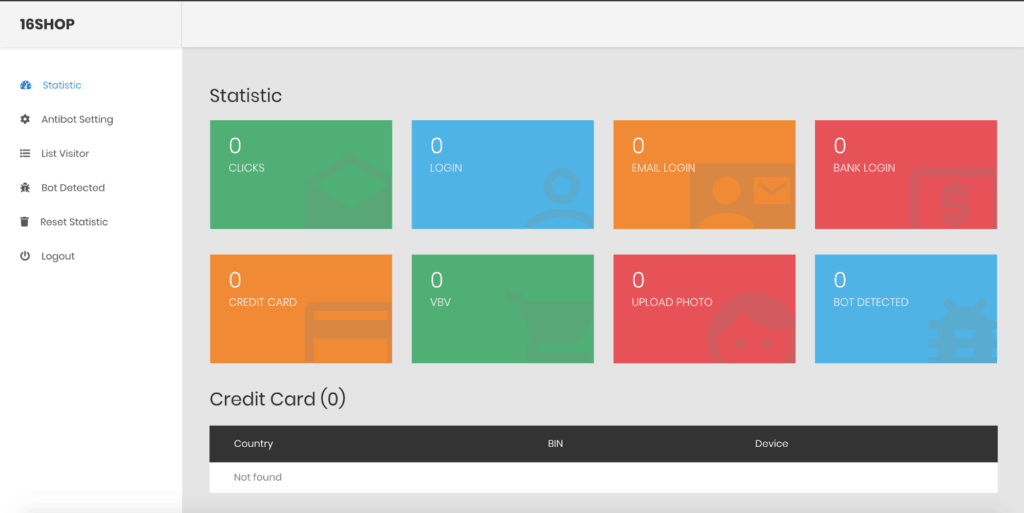
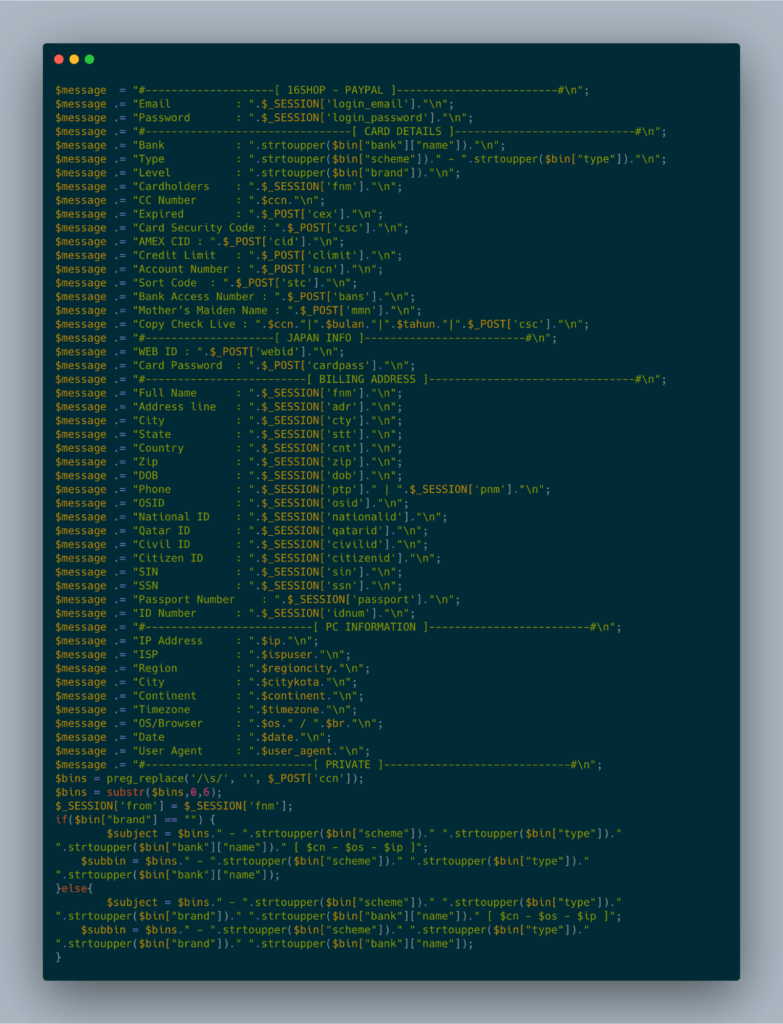
The buyer will be given a certain quota of deployment for phishing attacks. And if the limit is fulfilled, the buyer needs to repurchase the kit to continue. And to ease the buyer in using this, 16Shop crafted the kit so easily, yet sophisticated. The clean and simple UI is appealing to users that even layman can handle it. The phishing attacks launched by the user are guided perfectly with all the tools required. The dashboard is intuitive enough as any other analytics platform to show the real-time data updates regarding clicks, total information collected, bot detection etc. It allows the attacker to craft a phishing site as original looking and then send to the victim to respond. It’s by email means and has attachments within a click-bait. And if click to proceed, the malware steals details as victim’s login credentials, payment card details which includes owner’s name, expiration date, bank name, number, security code, and billing address with personally identifiable details. The new PayPal template also collects information about the victim’s IP address, ISP, browser, and geography too. After stealing the big data, it is then transported to hacker’s (buyer’s) controlled email box via Simple Mail Transfer Protocol. Image and Content Source: ZeroFOX